The Dig command is a powerful tool used to query DNS servers and obtain information about DNS records. In this article, we will explore how to install and use Dig on popular Linux distributions, and how to understand and manipulate the output. We will also demonstrate various use cases, including querying specific name servers, record types, and performing reverse DNS lookups.
How to Install dig Command
Before using the dig command in Linux, you need to ensure that it is installed on your system. You can check if the dig command is available on your system by typing the following command:
dig -v
If the dig command is installed on your system, the output should resemble the following:
DiG 9.11.3-1ubuntu1.1-Ubuntu
However, if dig is not present on your system, the command will print “dig: command not found”. In this case, you can install the dig tool using your distribution’s package manager. The process of installing dig may vary depending on the Linux distribution that you are using.
To install dig on Ubuntu and Debian, you can use the following command:
sudo apt update
sudo apt install dnsutilsThis will install the DNS utilities package, which includes the Dig command.
To install dig on CentOS and Fedora, you can use the following command:
sudo yum install bind-utilsThis will install the bind-utils package, which includes the Dig command.
To install dig on Arch Linux, you can use the following command:
sudo pacman -S bind-toolsThis will install the bind-tools package, which includes the Dig command.
Once the installation is complete, you can use the dig command to perform various DNS queries and lookups.
How to Understand the dig Command Output:
The Dig output contains several sections, including the question section, answer section, authority section, and additional section. Here is an example output for the domain “example.com“:
dig example.comOutput:
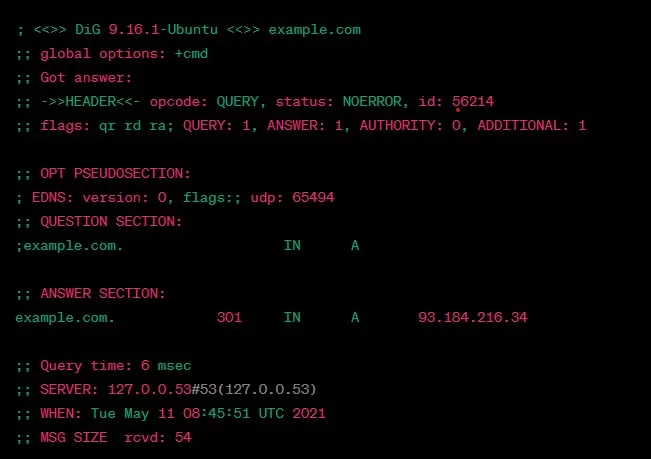
Here:
- Question section shows the domain name being queried and the record type requested (A in this case).
- Answer section shows the IP address of the domain name.
- Authority section shows the name servers responsible for the domain.
- Additional section shows additional information about the query.
Common options for dig command:
dig +nocmd: Suppresses the default output that shows the dig command and its options used to perform the query.dig +nocomments: Suppresses the comment section of the output, which includes a timestamp and the query ID.dig +noedns: Disables EDNS (Extension Mechanisms for DNS) queries, which are used to transfer larger packets over DNS. This option may be necessary if the authoritative server doesn’t support EDNS.dig +noquestion: Suppresses the question section of the output, which displays the domain name and record type being queried.dig +noanswer: Suppresses the answer section of the output, which displays the resource records returned by the DNS server.dig +noauthority: Suppresses the authority section of the output, which displays the authoritative DNS servers for the queried domain.dig +noadditional: Suppresses the additional section of the output, which displays additional resource records related to the query.dig +nostats: Suppresses the statistics section of the output, which displays query timing and network statistics.dig +short: Prints only the answer section of the output in a compact format.dig +trace: Traces the path of a DNS query from the root server to the authoritative server for the domain.dig +norecurse: Disables recursive querying, which means the command queries only the specified DNS server and not any other servers in the hierarchy.
How to Print Only the Answer Using dig Command
To print only the answer section, use the “+short” option:
dig example.com +short
Output:
93.184.216.34How to Query Specific Name Servers Using dig Command
To query a specific name server, use the “@server” option. Here is an example command querying the name server “ns1.exampledns.com” for the domain “example.com“:
dig example.com @ns1.exampledns.comOutput:
; <<>> DiG 9.16.1-Ubuntu <<>> example.com @ns1.exampledns.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29727
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;example.com. IN A
;; ANSWER SECTION:
example.com. 3600 IN A 93.184.216.34
;; Query time: 24 msec
;; SERVER: 192.168.0.1#53(192.168.0.1)
;; WHEN: Tue May 11 08:51:38 UTC 2021
;; MSG SIZE rcvd: 56Here:
- The “@ns1.exampledns.com” option specifies the name server to query.
- The “qr aa rd” flags indicate that the response is authoritative, meaning it comes directly from the name server responsible for the domain.
- The “WARNING: recursion requested but not available” message indicates that the name server does not support recursive queries.
How to Query a Record Type Using dig Command
Dig can query various record types, including A, CNAME, TXT, MX, NS, and more.
Querying A Records
To query A records, use the command below:
dig +nocmd example.com a +noall +answerOutput:
example.com. 301 IN A 93.184.216.34
You can also query the A record without specifying the a option.
dig +nocmd example.com +noall +answerQuerying CNAME Records
To query CNAME records, specify the record type as “CNAME”:
dig +nocmd www.example.com cname +noall +answerOutput:
www.example.com. 14399 IN CNAME example.com.
Querying TXT records
To query TXT records, specify the record type as “TXT”:
dig +nocmd example.com txt +noall +answerOutput:
example.com. 21599 IN TXT "v=spf1 include:_spf.example.com ~all"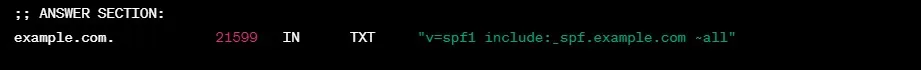
Querying MX Records
To query MX records, specify the record type as “MX”:
dig +nocmd example.com mx +noall +answer
Output:
example.com. 21599 IN MX 1 aspmx.l.google.com.
example.com. 21599 IN MX 10 alt4.aspmx.l.google.com.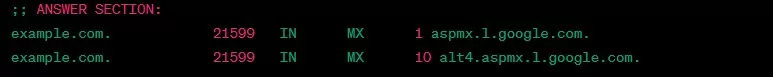
Querying NS Records
To query NS records, specify the record type as “NS”:
dig +nocmd example.com ns +noall +answer
Output:
example.com. 21599 IN NS b.iana-servers.net.
example.com. 21599 IN NS f.iana-servers.net.
example.com. 21599 IN NS a.iana-servers.net.
example.com. 21599 IN NS e.iana-servers.net.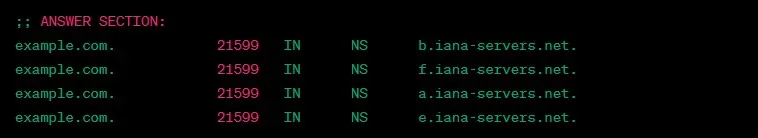
Querying All Records
To query all available records for a domain, use the ANY record type:
dig +nocmd example.com any +noall +answer
Output:
example.com. 21599 IN SOA a.iana-servers.net. hostmaster.root-servers.org. 2021112152 1800 900 604800 3600
example.com. 21599 IN A 93.184.216.34
example.com. 21599 IN NS b.iana-servers.net.
example.com. 21599 IN NS f.iana-servers.net.
example.com. 21599 IN NS a.iana-servers.net.
example.com. 21599 IN NS e.iana-servers.net.
example.com. 21599 IN MX 1 aspmx.l.google.com.
example.com. 21599 IN MX 10 alt4.aspmx.l.google.com.
example.com. 21599 IN TXT "v=spf1 include:_spf.example.com ~all"
example.com. 21599 IN AAAA 2606:2800:220:1:248:1893:25c8:1946
example.com. 21599 IN AAAA 2606:2800:220:1:248:1893:25c8:1947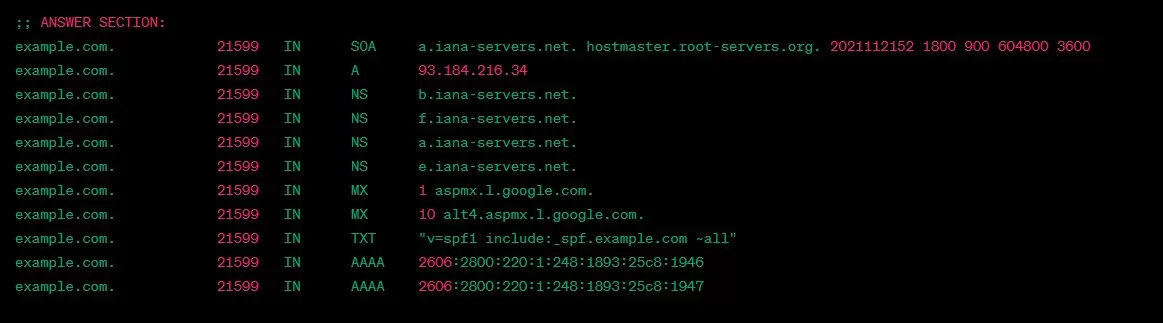
Reverse DNS Lookup Using dig Command
A reverse DNS lookup is used to determine the domain name associated with a given IP address. This is useful for troubleshooting purposes or for identifying potential security threats. To perform a reverse DNS lookup using dig, simply specify the IP address in the query:
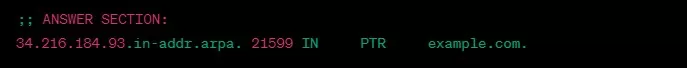
dig -x 93.184.216.34 +noall +answerOutput:
34.216.184.93.in-addr.arpa. 21599 IN PTR example.com.The above output shows that the domain name associated with the IP address 93.184.216.34 is example.com.
Bulk Queries Using dig Command
It is often useful to perform multiple queries at once, especially if you need to check several domains or records at the same time. One way to do this is to create a text file containing all the queries you want to perform, with each query on a separate line. You can then pass this file to dig using the -f option. For example, let’s say we have a file called domains.txt containing the following list of domains:
example.com
google.com
yahoo.comWe can query the A records for all these domains at once using the following command:
dig -f domains.txt +noall +answerOutput:
example.com. 21599 IN A 93.184.216.34
google.com. 299 IN A 172.217.166.46
yahoo.com. 284 IN A 98.137.11.163The above output shows that the A records for example.com, google.com, and yahoo.com have been returned.
Conclusion
Dig is a powerful command-line tool that is used to perform DNS lookups. It can be used to query various DNS record types, including A records, MX records, NS records, TXT records, and SOA records, among others. Dig is also useful for troubleshooting DNS issues and for performing bulk queries. Understanding how to use dig effectively can be an invaluable skill for network administrators and web developers alike.
Got questions or suggestions on the article? Don’t hesitate to leave a comment below. Your feedback is valuable to us and helps improve the content quality. And don’t forget to share this article with others who might find it useful. Looking forward to hearing from you!
If our tutorials helped you, please consider buying us a coffee. We appreciate your support!
Thank you for your support.



